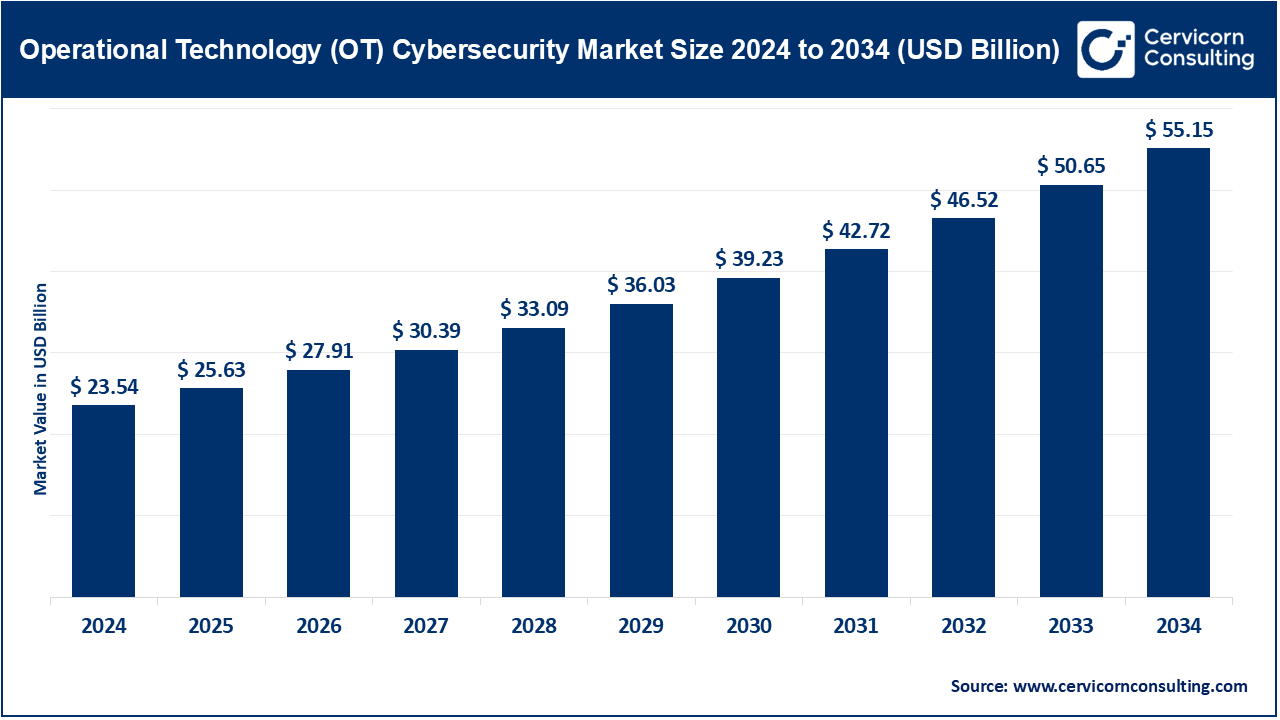
The global operational technology (OT) cybersecurity market size was valued at USD 23.54 billion in 2024 and is anticipated to reach around USD 55.15 billion by 2034, growing at a compound annual growth rate (CAGR) of 16.4% over the forecast period from 2025 to 2034. The OT Cybersecurity market is undergoing a growth spurt as more industries adopt connections to their operations through connected devices, Industrial Internet of Things (IIoT) and intelligent automation. In the era of IT and OT convergence, critical infrastructure, including power grid, manufacturing facilities, transportation and water treatment plants has moved to become on the top list of concerns in need of security. It is one of the most important trends in the cybersecurity sphere today due to the growing cases of cyber-attacks against industrial control systems (ICS) and supervisory control and data acquisition (SCADA) networking giving rise to organizations adopting advanced OT security solutions.
The operational technology (OT) cybersecurity is offered under a more comprehensive industrial security direction to protect physical processes, machinery, and industrial control systems against viral assaults, unauthorized entrance, and invasions to the operations. It includes threat detection, real-time monitoring, network segmentation, incident response, and compliance management in the unique needs of operator environments. Energy, oil & gas, transportation, and manufacturing are all sectors that implement these solutions to keep operations intact, safe, and compliant with regulation as they protect against internal and external cyber risks.
Report Scope
| Area of Focus | Details |
| Market Size in 2025 | USD 25.63 Billion |
| Expected Market Size in 2034 | USD 55.15 Billion |
| Projected CAGR 2025 to 2034 | 16.40% |
| Leading Region | North America |
| Fastest Growing Region | Asia-pacific |
| Key Segments | Component, Security Type, Deployment Mode, Enterprise Size, Offering, End-User Industry, Region |
| Key Companies | Cisco Systems, Inc., Palo Alto Networks, Inc., Fortinet, Inc., Check Point Software Technologies Ltd., IBM Corporation, Siemens AG, Honeywell International Inc., Dragos Inc., Claroty Ltd., Nozomi Networks Inc. |
Solutions: OT cybersecurity solutions are hardware and software applications implemented to safeguard networks and systems against cyberattack on industrial equipment and devices. They will be concentrated on prevention, detection, and immediate reaction in the operation environments. One European power grid operator in April 2025 implemented a more advanced intrusion detection system inside its SCADA network that improves real time anomaly detection. This upgrade prevented various unauthorized control attempts and made the supply of power uninterrupted. The action showed how essential solutions were in contemporary OT security.
OT Cybersecurity Market Share, By Component, 2024 (%)
| Component | Revenue Share, 2024 (%) |
| Solutions | 71.20% |
| Services | 28.80% |
Services: The offered services cover consulting, integration, training, and maintenance so that OT security systems could be deployed and maintained. They introduce outside skills that are not usually present internally. The vulnerability assessment and patch program was a one-year-long arrangement by a North American manufacturer in November 2024 to acquire the services of a cybersecurity services company. This process determined and resolved 37 vulnerabilities that were not patched on their industrial control systems. Intervention cut down cyber-related down time by 28.2%.
Network Security: OT network security protects the channels of communication between devices, systems and access to the outside connection. It employs the use of segmentation, firewalls and secure protocols in order to avoid unauthorized access. In June 2025, a Middle Eastern oil refinery deployed network segmentation used to separate safety systems with corporate IT networks. This architecture prevented the spread of a ransomware across the operational controls. The plan strengthened the defense against any specific cyberattacks.
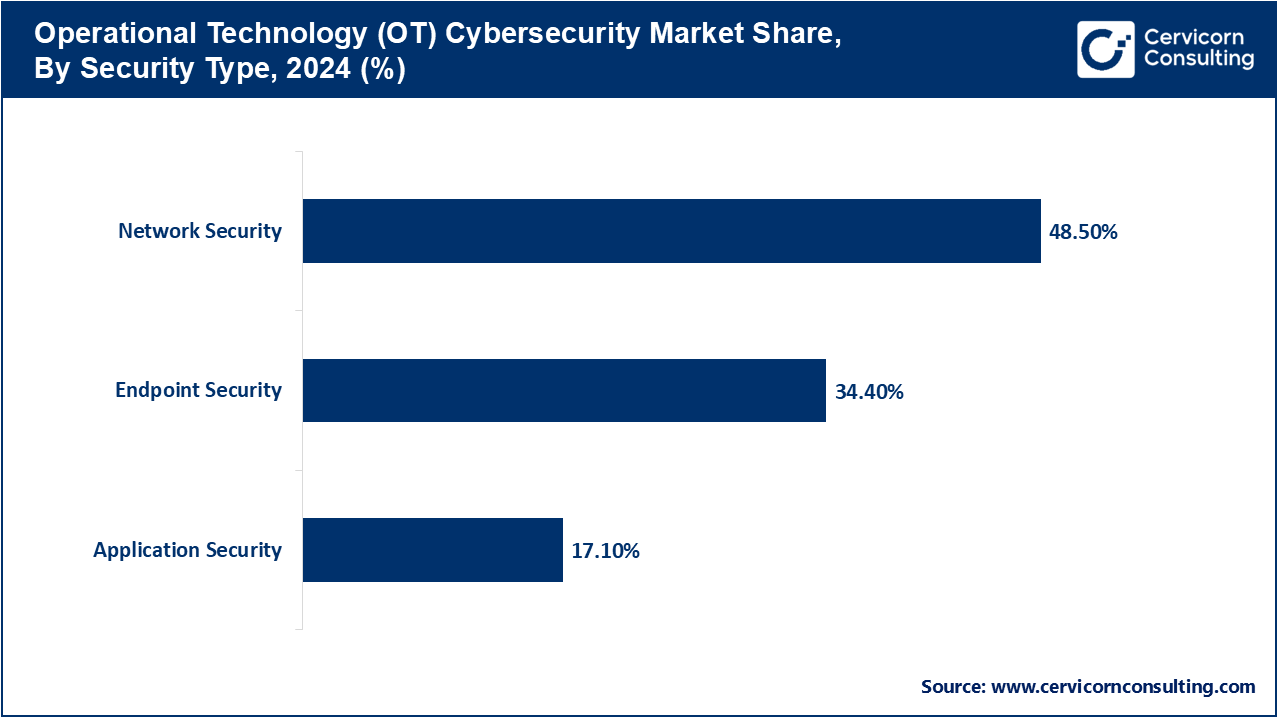
Endpoint Security: Endpoint security is less about OT devices as a whole than protecting individual OT endpoints such as PLCs, HMIs, and sensors against malware or unauthorized changes. It comprises antivirus, patching and authentication. In March 2024, one Japanese rail transit company deployed endpoint agents to more than 1,000 track-monitoring equipment. This prevented malware, in case of a cyber hacking bid, to manipulate control signals data. Consequently, the activities of the trains were not affected.
Application Security: Application security is applied to make the OT softwares applications work safely, including vulnerabilities in code and configuration. It has patching, testing and run time protection. In August 2025, a worldwide mining corporation resolved to offer protection to its predictive maintenance software after a security audit. The patch also stopped the possibility of unauthorized access to the settings of equipment control. This ensured key machinery was not sabotaged.
On-Premises: On-premises-based deployments occur inside the facilities of the organization where the company has complete control and increased maintenance requirements. In May 2024, a plant at Canadian hydroelectric facility deployed an industry on-site monitoring system as a part of meeting national security regulations. This strategy promoted the retention of sensitive data on operations within facility confines. It also conformed well with severe regulations of data sovereignty.
OT Cybersecurity Market Share, By Deployment Type, 2024 (%)
| Deployment Type | Revenue Share, 2024 (%) |
| On-Premises | 59% |
| CLoud | 41% |
Cloud: The implementation of cloud provides OT security on the external servers, which allows scaling and fast updating. In January 2025, the migration of SIEM platform in the cloud in Southeast Asian smart factory took place. This cut down the update periods to hours and enhanced integration by use of live threat intelligence feeds. The change improved security services provided by numerous manufacturing facilities.
Energy & Utilities: The energy & utilities segment has generated highest revenue share. This segment secures power grid, water treatment plants and pipelines against cyber-attacks and guarantees resilience of critical infrastructure. In February 2025, a utility corporation in South America installed OT firewalls to protect controls of water distribution. The system prevented an intrusion that was targeted at changing the level of treatment on chlorine. This helped to avoid a possible health epidemic.
Manufacturing: Manufacturing OT cybersecurity protects production lines, robotics, and industrial IoT against cyberattacks that may stop production. In July 2024, one of the European automotive plants used to implement the anomaly detection into assembly robots. It also detected the possibility of an abnormal activity as a result of a malware, and thus gave an opportunity to delete it speedily. There was slight postponement in production.
Transportation & Logistics: The domain protects railways, ports, and logistics systems against cyber attacks that cause disruptions to the operations. In October 2024, a U.S. port high in crane control vulnerability had secure gates installed on crane control. These thwarted unauthorized intrusion of wireless access which would have led to mishandling of cargo. The solution increased the safety of operations.
Managed Security Services: Managed services does outsource OT monitoring, detection and response to third parties specialized in it. An Asian oil and gas giant entered into a multi year contract with a managed security provider in December 2024. The first month, the team identified and prevented unauthorized PLC configuration changes This eliminated expensive periods of operation.
Professional Services: Professional services offer design, deployment, and consulting services that are specific to certain OT environments. In March 2025, one of the European drug companies recruited experts to re-architect an OT network. The update limited the lateral attack vectors and checked the compliance of the programs. This helped the security and regulatory status.
North America has accelerated the adoption of OT Cybersecurity based on advancements in industrial automation and critical infrastructure. Firms are deploying AI based detection and monitoring technologies, real-time monitoring technologies, and routing response technologies. Establishing strategic partnerships and investing in protecting industrial IoT Cybersecurity also leads to enhance resilience, and decrease in downtime for OT networks across energy, manufacturing, and utility sectors.
The drivers of OT Cybersecurity in Europe are IT/OT convergence compliance, modernization of digital infrastructures, and Industry 4.0 adoption. Companies focus on AI-enabled threat detection and on other novel attack technologies, continuous monitoring deployment for industrial control systems, and proactive and dynamic vulnerability management. Government policies and international cross-border cybersecurity policies are pushing organizations to adopt and invest in better OT security frameworks, thereby improving operational resilience and risk exposure in critical areas such as manufacturing, energy, and transport.
The Asia-Pacific region is growing rapidly due to the adoption of industrial automation, and the modernization of digitized factories in addition to government-sponsored digital transformation initiatives. Companies are adopting AI-driven micromanagement systems which integrate monitoring, responding to and the mitigation of risks in control systems prevalent in industrial environments. The region's emphasis on the protection of critical infrastructure has resulted in heightened operational technology security practices which improve system performance, resilience, and compliance.
OT Cybersecurity Market Share, By Region, 2024 (%)
| Region | Revenue Share, 2024 (%) |
| North America | 37.70% |
| Europe | 24.20% |
| Asia-Pacific | 29.80% |
| LAMEA | 8.30% |
In LAMEA is growing due to emergent infrastructure development, digitized industrial processes, and regulatory policies. Industries are adopting defense in depth strategies in which integrated protective systems within which real-time monitoring, industrial network intrusion detection, and risk mitigation are performed. These systems are designed for use with energy, mining, and utility sectors' interdependent critical function continuity.
Market Segmentation
By Component
By Security Type
By Deployment Mode
By Enterprise Size
By Offering
By End-User Industry
By Region